Use your Battery and Siri to help protect your privacy !

Siri is great! She’s informative and funny at parties to ask silly questions like “Hey Siri, What does Siri mean?”. Truth be told Siri is not your friend. She is always listening and telling other what you’re talking about. You’d kick any other friend like that to the curb. So why do you let Siri listen to everything you do? Did you read Orwell’s 1984 and think, “Hey that’s a great idea!”?
Back in August of 2019, Apple issued a formal apology for allowing humans to listen to Siri recordings. It is tough to stay ahead of all of the changes in technology and their impact on privacy and user’s lives. Companies have to walk a fine line between what is functional versus an invasion of privacy.
Recently, at a training event I was asked about ads that were appearing in people’s feeds whose content came, not from what was typed into a Google search, but what was said aloud in conversation. How could an ad for French Onion pop up when you were just discussing it?
Siri not only operates independently but also within each app. In order to have Siri stop listening to you’ll need to disable Ask Siri, Siri Suggestions, and go into each app to make sure Siri is disabled.
If you read through the Siri Privacy Statement you’ll see that Siri is trying to learn how you use your device including your browsing history, emails, messages, contacts, and other information. You shouldn’t be shocked by this and if you are, be aware that most apps operate this way. They need the data to operate and be improved yet some companies share that data to improve their advertiser’s experience.
In order to turn off Siri you’ll want to go into Settings, Siri & Search, then disable ‘Listen for Hey Siri’ as well as ‘Press Side Button For Siri’, ‘Suggestions in Search’, ‘Suggestions in Lookup’, and ‘Suggestions in Lock Screen’. Below that you’ll see a listing of all your apps that use Siri Suggestions.
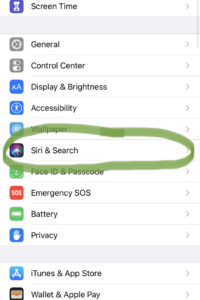
My suggestion is to go into each app and disable Learn from this App, Show in Search, and Show App. Next, go to Settings and then Privacy and scroll to the bottom to click on Analytics & Improvements to turn off Share iPhone Analytics, Improve Siri & Dictation, as well as, Share iCloud Analytics.
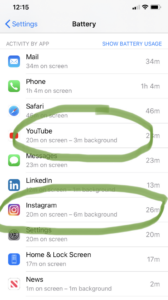
Apps are constantly running in the background mining data and using your battery power. If you go to ‘Settings’ on your iPhone and then click on ‘Battery’ and scroll down past ‘Low Power Mode’, and ‘Battery Health’ to ‘Battery Usage by App’ which will show percentage of battery usage by app plus the time the app was active including time the app was operating in the background. You can click on both ‘Show Activity’ or ‘Show Usage’.
You’ll always need to negotiate between functionality and privacy so it’s up to you to determine what you’re willing to share and what you want to get for it. Some people choose to post a lot of their information to social media and make it publicly available while others have their profiles set to private and rarely post if at all. That’s your decision to make but the goal of Security Awareness Training is to make you mindful of the trade-offs that come with your decisions.